Protocols & Port in Networking
What is a protocol ?
A network protocol is an established set of rules that determine how data is transmitted between different devices in the same network.
Essentially it allows connected devices to communicate with each other regardless of any difference in their internal process,structure or design.
Types of Protocol
TCP
POP
HTTP
SMTP
SSL
FTP
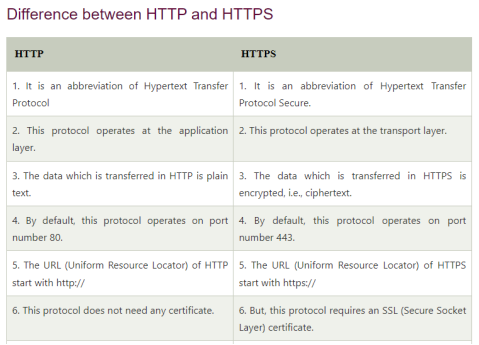
HTTP:
1. Hyper Text Transfer Protocol
2. It is an application layer protocol for transmitting hypermedia documents such as HTML.
3. It was designed for communicating between web browsers and web servers,but it can also be used for other purposes.
4. HTTP is one of the most commonly used application-level protocol used for hyper-text data distribution, collaboration, and hypertext information system.
5. HTTP is abbreviated as Hypertext Transfer Protocol, an application layer protocol used primarily with the WWW (World Wide Web) in the client-server model where a web browser is a client communicating with the webserver which is hosting the website. Since 1990, this has become the foundation for data communication. HTTP is a standard and stateless protocol that is used for different purposes as well using extensions for request methods, error codes, as well as headers.
6. HTTP is a communication protocol which is employed for delivering data (usually HTML files, multimedia files, etc.) on the World Wide Web through its default TCP port 80. However, there are other ports also which can be implemented for this function. HTTP has two different versions, HTTP/1.0, which is the old one and the newest HTTP/1.1. In its older version, a separate connection was required. In the case of a new version, the same connection can be recycled several times.
Steps involved in HTTP request:
A necessary HTTP request has the following steps:
Initially, a link to the HTTP server gets opened.
Then a request is sent.
It does some processing on the server.
Once the request processing is done, the response is sent back from the server.
Finally, the connection is closed.
Architecture of HTTP

The HTTP is meant for request/response depending on a client-server architecture where the user requests information through a web browser to the web server, which then responds to the requested data.
Web Client: The client of this client-server architecture asks for a request to a specific server through the HTTP (TCP/IP connection) as a request method in the form of a URL. It also contains a MIME-like message that contains request modifier and client information.
Web Server: This accepts the request and process with a response by a status line, together with the version of the message’s protocol as well as the success or error code, followed by a MIME-like message having server information, some metadata, and possible the entity-body content holding the requested information.
Feature of HTTP
· HTTP is connection less: An HTTP request is initiated by the browser (HTTP client) as per the user’s request for information. The server will process the request and launch back with a response which the client waits for.
· HTTP is simple: HTTP/2 does the encapsulation of HTTP messages into frames; i.e., HTTP is typically designed to be plain and human-readable.
· HTTP is extensible/customized: HTTP can be integrated with new functionality by providing a simple agreement between a client and a server.
· HTTP is stateless, but not sessionless: HTTP is stateless, which means there is no connection among two requests being consecutively carried out on the same connection. However, when the core of HTTP is itself a stateless one, HTTP cookies provide in making use of stateful sessions. Through the concept of header extensibility, HTTP cookies can be incorporated into the workflow, making session creation on each HTTP request for sharing the same content.
HTTPS
1. Hypertext Transfer Protocol Secure
2. It is an extension of the hypertext transfer protocol
3. It is used for secure communication over a computer network and is widely used on internet.
4. HTTPS is an abbreviation of Hypertext Transfer Protocol Secure. It is a secure extension or version of HTTP. This protocol is mainly used for providing security to the data sent between a website and the web browser. It is widely used on the internet and used for secure communications. This protocol uses the 443 port number for communicating the data.
5. This protocol is also called HTTP over SSL because the HTTPS communication protocols are encrypted using the SSL (Secure Socket Layer).
6. By default, it is supported by various web browsers.
7. Those websites which need login credentials should use the HTTPS protocol for sending the data.

Advantages of HTTPS:
Following are the advantages or benefits of a Hypertext Transfer Protocol Secure (HTTPS):
The main advantage of HTTPS is that it provides high security to users.
Data and information are protected. So, it ensures data protection.
SSL technology in HTTPS protects the data from third-party or hackers. And this technology builds trust for the users who are using it.
It helps users by performing banking transactions.
Disadvantages of HTTPS:
Following are the disadvantages or limitations of a Hypertext Transfer Protocol Secure (HTTPS):
The big disadvantage of HTTPS is that users need to purchase the SSL certificate.
The speed of accessing the website is slow because there are various complexities in communication.
Users need to update all their internal links.
SSH
1. Secure shell
2. It is a network communication protocol that enables two computers to communicate and share data
3. SSH(Secure Shell) is access credential that is used in the SSH Protocol. In other words, it is a cryptographic network protocol that is used for transferring encrypted data over network. It allows you to connect to a server, or multiple servers, without having you to remember or enter your password for each system that is to login remotely from one system into another.
It always comes in key pair:
Public key — Everyone can see it, no need to protect it. (for encryption function)
Private key — Stays in computer, must be protected. (for decryption function)
Key pairs can be of the following types:
User Key — If public key and private key remain with the user.
Host Key — If public key and private key are on a remote system.
Session key — Used when large amount of data is to be transmitted.
FTP
1. It is a standard communication protocol used for the transfer of computer files from a server to a client on a computer network.
2. File transfer protocol (FTP) is an Internet tool provided by TCP/IP. The first feature of FTP is developed by Abhay Bhushan in 1971. It helps to transfer files from one computer to another by providing access to directories or folders on remote computers and allows software, data, text file to be transferred between different kinds of computers. The end-user in the connection is known as localhost and the server which provides data is known as the remote host.
The goals of FTP are:
It encourages the direct use of remote computers.
It shields users from system variations (operating system, directory structures, file structures, etc.)
It promotes sharing of files and other types of data.
DNS

1. It is the hierarchical and decentralized naming system used to identify computer reachable through the internet or other IP network.
2. The Domain Name System (DNS) turns domain names into IP addresses, which browsers use to load internet pages. Every device connected to the internet has its own IP address, which is used by other devices to locate the device. DNS servers make it possible for people to input normal words into their browsers, such as Fortinet.com, without having to keep track of the IP address for every website.
DHCP
1) Dynamic Host Configuration Protocol
2) It is a client/server protocol that automatically provides an ip host with its IP address and other realted configuration information such as the subnet mask & default gateway.
3) DHCP (Dynamic Host Configuration Protocol) is a protocol that provides quick, automatic, and central management for the distribution of IP addresses within a network. It’s also used to configure the subnet mask, default gateway, and DNS server information on the device.
How DHCP Works?

a) A DHCP server issues unique IP addresses and automatically configures other network information. In most homes and small businesses, the router acts as the DHCP server. In large networks, a single computer might take on that role. To make this work, a device (the client) requests an IP address from a router (the host). Then, the host assigns an available IP address so that the client can communicate on the network.
b) When a device is turned on and connected to a network that has a DHCP server, it sends a request to the server, called a DHCPDISCOVER request.
c) After the DISCOVER packet reaches the DHCP server, the server holds on to an IP address that the device can use, then offers the client the address with a DHCPOFFER packet.
d) Once the offer has been made for the chosen IP address, the device responds to the DHCP server with a DHCPREQUEST packet to accept it. Then, the server sends an ACK to confirm that the device has that specific IP address and to define the amount of time that the device can use the address before getting a new one.
e) If the server decides that the device cannot have the IP address, it will send a NACK.
What is DHCP snooping?
DHCP snooping is a layer two security technology that stops any DHCP traffic that it defines as unacceptable. The snooping technology, built into the network switch operating system, prevents unauthorized DHCP servers from offering IP addresses to DHCP clients.
What is DHCP relay?
A relay agent is a host that forwards DHCP packets between clients and servers. A network administrator can use relay agents to forward requests and replies between clients and servers not on the same physical subnet.
ICMP


1. Internet Control Manage Protocol
2. It is a protocol that devices within a network use to communicate problem with data transmission.
3. ICMP (Internet Control Message Protocol) is a network layer protocol that reports errors and provides information related to IP packet processing. ICMP is used by network devices to send error messages indicating, for example, that a requested service is not available or that a host isn’t reachable
4. ICMP is commonly used by network tools such as ping or traceroute. Consider the following example that illustrates how ping can be used to test the reachability of a host:
5. Host A wants to test whether it can reach Server over the network. Host A will start the ping utility that will send ICMP Echo Request packets to Server. If Server is reachable, it will respond with ICMP Echo Reply packets. If Host A receives no response from Server, there might be a problem on the network.
6. One other common ICMP message is the Destination unreachable message. Here is an example:
7. Host A sends a packet to Host B. Because the Host B is down, the router will send an ICMP Destination host unreachable message to Host A, informing it that the destination host is unreachable, e.g.:

NOTE
ICMP messages are encapsulated in IP datagrams, which means that they don’t use higher level protocols (such as TCP or UDP) for transmission.
ARP

1) Address Resolution Protocol
2) It is a protocol or procedure that connects an ever-changing IP address to a fixed physical machine address,also known as MAC address,in a LAN.
3) Most of the computer programs/applications use logical address (IP address) to send/receive messages, however, the actual communication happens over the physical address (MAC address) i.e from layer 2 of the OSI model. So our mission is to get the destination MAC address which helps in communicating with other devices. This is where ARP comes into the picture, its functionality is to translate IP address to physical addresses.
4) The acronym ARP stands for Address Resolution Protocol which is one of the most important protocols of the Network layer in the OSI model.
5) Note: ARP finds the hardware address, also known as Media Access Control (MAC) address, of a host from its known IP address.
MAC

1. Media Access Control
2. It is a unique identifier assigned to a network interface card for use as a network address in communication within a network segment.
3. MAC address is the physical address, which uniquely identifies each device on a given network. To make communication between two networked devices, we need two addresses: IP address and MAC address. It is assigned to the NIC (Network Interface card) of each device that can be connected to the internet.
4. It stands for Media Access Control, and also known as Physical address, hardware address, or BIA (Burned In Address).
5. It is globally unique; it means two devices cannot have the same MAC address. It is represented in a hexadecimal format on each device, such as 00:0a:95:9d:67:16.
6. It is 12-digit, and 48 bits long, out of which the first 24 bits are used for OUI(Organization Unique Identifier), and 24 bits are for NIC/vendor-specific.
7. It works on the data link layer of the OSI model.
8. It is provided by the device’s vendor at the time of manufacturing and embedded in its NIC, which is ideally cannot be changed.
9. The ARP protocol is used to associate a logical address with a physical or MAC address.
Why should the MAC address be unique in the LAN network?
If a LAN network has two or more devices with the same MAC address, that network will not work.
Suppose three devices A, B, and C are connected to a network through a switch. The MAC addresses of these devices are 11000ABB28FC, 00000ABB28FC, and 00000ABB28FC, respectively. The NIC of devices B and C have the same MAC address. If device A sends a data frame to the address 00000ABB28FC, the switch will fail to deliver this frame to the destination, as it has two recipients of this data frame.
Format of MAC address
As we have already discussed in the above section, we cannot assign the MAC address to the device’s NIC; it is preconfigured by the manufacturers. So, let’s understand how it is configured and what format is selected.
It is 12 digits or 6-byte hexadecimal number, which is represented in colon-hexadecimal notation format. It is divided into six octets, and each octet contains 8 bits.
The first three octets are used as the OUI or Organisationally Unique Identifier. These MAC prefixes are assigned to each organization or vendor by the IEEE Registration Authority Committee.
Some example of OUI of known vendors are:
CC:46:D6 — Cisco
3C:5A:B4 — Google, Inc.
3C:D9:2B — Hewlett Packard
00:9A:CD — HUAWEI TECHNOLOGIES CO.,LTD

Reason to have both IP and MAC addresses.
As we already had the IP address to communicate a computer to the internet, why we need the MAC address. The answer to this question is that every mac address is assigned to the NIC of a hardware device that helps to identify a device over a network.
When we request a page to load on the internet, the request is responded and sent to our IP address.
Both MAC and IP addresses are operated on different layers of the internet protocol suite. The MAC address works on layer 2 and helps identify the devices within the same broadcast network (such as the router). On the other hand, the IP addresses are used on layer 3 and help identify the devices on different networks.
We have the IP address to identify the device through different networks, we still need a MAC address to find the devices on the same network.
TCP v/s UPD
TCP
1) Transmission Control Protocol
2) It is a standard way of communication that enables application programs and computing devices to exchange messages over a network.
3) TCP stands for Transmission Control Protocol. It is a transport layer protocol that facilitates the transmission of packets from source to destination. It is a connection-oriented protocol that means it establishes the connection prior to the communication that occurs between the computing devices in a network. This protocol is used with an IP protocol, so together, they are referred to as a TCP/IP.
4) The main functionality of the TCP is to take the data from the application layer. Then it divides the data into a several packets, provides numbering to these packets, and finally transmits these packets to the destination. The TCP, on the other side, will reassemble the packets and transmits them to the application layer. As we know that TCP is a connection-oriented protocol, so the connection will remain established until the communication is not completed between the sender and the receiver.
UDP
1. User Datagram Protocol
2. It refers to a protocol used for communication throughout the internet.
3. It is specifically chosen for time-sensitive application like gaming,streaming,live or dns lookup.
4. The User Datagram Protocol, or UDP, is a communication protocol used across the Internet for especially time-sensitive transmissions such as video playback or DNS lookups. It speeds up communications by not formally establishing a connection before data is transferred. This allows data to be transferred very quickly, but it can also cause packets to become lost in transit — and create opportunities for exploitation in the form of DDoS attacks.
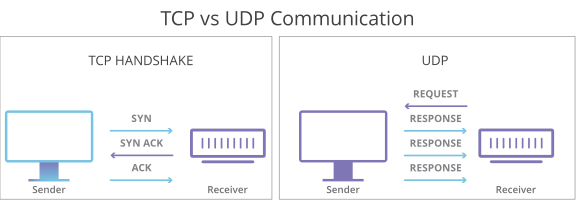
TCP Three way Handshake

This could also be seen as a way of how TCP connection is established. Before getting into the details, let us look at some basics. TCP stands for Transmission Control Protocol which indicates that it does something to control the transmission of the data in a reliable way.
The process of communication between devices over the internet happens according to the current TCP/IP suite model(stripped out version of OSI reference model). The Application layer is a top pile of a stack of TCP/IP models from where network referenced applications like web browsers on the client-side establish a connection with the server. From the application layer, the information is transferred to the transport layer where our topic comes into the picture. The two important protocols of this layer are — TCP, UDP(User Datagram Protocol) out of which TCP is prevalent(since it provides reliability for the connection established). However, you can find an application of UDP in querying the DNS server to get the binary equivalent of the Domain Name used for the website.
TCP provides reliable communication with something called Positive Acknowledgement with Re-transmission(PAR). The Protocol Data Unit(PDU) of the transport layer is called a segment. Now a device using PAR resend the data unit until it receives an acknowledgement. If the data unit received at the receiver’s end is damaged(It checks the data with checksum functionality of the transport layer that is used for Error Detection), the receiver discards the segment. So the sender has to resend the data unit for which positive acknowledgement is not received. You can realize from the above mechanism that three segments are exchanged between sender(client) and receiver(server) for a reliable TCP connection to get established.
Let us delve into how this mechanism works :
Step 1 (SYN): In the first step, the client wants to establish a connection with a server, so it sends a segment with SYN(Synchronize Sequence Number) which informs the server that the client is likely to start communication and with what sequence number it starts segments with
Step 2 (SYN + ACK): Server responds to the client request with SYN-ACK signal bits set. Acknowledgement(ACK) signifies the response of the segment it received and SYN signifies with what sequence number it is likely to start the segments with
Step 3 (ACK): In the final part client acknowledges the response of the server and they both establish a reliable connection with which they will start the actual data transfer
TCP Flags
TCP flags are used to indicate a particular state during a TCP conversation. TCP flags can be used for troubleshooting purposes or to control how a particular connection is handled.
TCP flags are various types of flag bits present in the TCP header. Each of them has its own significance. They initiate connections, carry data, and tear down connections. The commonly used TCP flags are syn, ack, rst, fin, urg, psh. We will discuss the details later.
TCP Flags List
SYN (synchronize): Packets that are used to initiate a connection.
ACK (acknowledgment): Packets that are used to confirm that the data packets have been received, also used to confirm the initiation request and tear down requests
RST (reset): Signify the connection is down or maybe the service is not accepting the requests
FIN (finish): Indicate that the connection is being torn down. Both the sender and receiver send the FIN packets to gracefully terminate the connection
PSH (push): Indicate that the incoming data should be passed on directly to the application instead of getting buffered
URG (urgent): Indicate that the data that the packet is carrying should be processed immediately by the TCP stack
3 Additional TCP Flags
These CWR ECE NS TCP flags are not commonly used.
CWR (congestion window has been reduced). Indicates that the sending host has received a TCP segment with the ECE flag set. The congestion window is an internal variable maintained by TCP to manage the size of the send window.
ECE (TCP peer is ECN-capable).
Indicates that a TCP peer is ECN-capable during the TCP 3-way handshake and to indicate that a TCP segment was received on the connection with the ECN field in the IP header set to 11.
NS (1 bit): ECN-nonce — concealment protection
Protocols & Ports
A network protocol is an established set of rules that determine how data is transmitted between different devices in the same network.Essentially,it allows connected devices to communicate with each other,regardless of any differences in their internal process,structure or design.
A port in networking is a software defined number associated to a network protocol that receives or transmits communication for a specific service.So IP address+port defines address of the particular service on the particular system.Thus ranging is 0–65535. Port no 0 is reserved & cannot be used.
Ports are divided into three:
1. The well known port
a) 0–1023
b) These are allocated to server services by the internet assigned number authority(IANA).
c) Ex: Web server normally use port 80
d) SMTP-port 25
2. Registered port
a) 1024–49151
b) These can be registered for services with IANA & should be treated as semi-reserved.
c) User written programs should not use these.
3. Dynamic port/private port
a) 49125–65535
b) Free to use in client program
c) When a web browser connects to a web server the browser will allocate itself a port in this range .
d) Also known as ephemeral ports
What is the difference between a port number and a protocol number?
You can think of a port as a phone extension, with the computer’s IP address being like its phone number. You can call the number (IP address) to talk to the computer, then dial the extension (port) to talk to a specific application. An application needs to be listening on a port in order to communicate.
A protocol is just the language that the two applications on either end of a conversation agree to speak in. If your application is sending streams of bytes to my application, my application needs to know how to interpret those bytes.
A protocol is an agreement on how to interpret data and how to respond to messages. They generally specify message formats and legal messages. Examples of protocols include:
·TCP/IP
·HTTP
·SSH
A port is part of socket end point in TCP and UDP. They allow the operating system to distinguish which TCP or UDP service on the host should receive incoming messages.
The confusion generally arises because, a number of ports are reserved (eg. port 80) and are generally listened to by severs expecting a particular protocol (HTTP in the case of port 80). While messages send to port 80 are generally expected to be HTTP messages, there is nothing stopping an non-HTTP server from listening on port 80 or an HTTP server from listening on an alternative port (for example 8080 or 8088).
A protocol is a specification for how two devices should exchange data in a way that they can both understand. A port is kind of a numbered ‘tag’ that helps a computer decide who should receive an incoming piece of data.
Many protocols have a port that they run on by default; this makes it easier to discover them or configure applications that use them. But that’s not a hard rule; they could always listen on a different port, as long as anyone contacting them knew about the change.
In Simple port means to whom you communicate. & Protocol means how to communicate or way of communication.
A port is just a channel that you select for the communication, and the protocol determines how the communication is done. A certain protocol usually uses a specific port, like port 80 for HTTP, port 21 for FTP.

what is telnet?
TELNET stands for TErminaL NETwork. It is a type of protocol that enables one computer to connect to local computer. It is a used as a standard TCP/IP protocol for virtual terminal service which is given by ISO. Computer which starts connection known as the local computer. Computer which is being connected to i.e. which accepts the connection known as remote computer. When the connection is established between local and remote computer. During telnet operation whatever that is being performed on the remote computer will be displayed by local computer. Telnet operates on client/server principle. Local computer uses telnet client program and the remote computers uses telnet server program.
The main task of the internet is to provide services to users. For example, users want to run different application programs at the remote site and transfers a result to the local site. This requires a client-server program such as FTP, SMTP. But this would not allow us to create a specific program for each demand.
The better solution is to provide a general client-server program that lets the user access any application program on a remote computer. Therefore, a program that allows a user to log on to a remote computer. A popular client-server program Telnet is used to meet such demands. Telnet is an abbreviation for Terminal Network.
Telnet provides a connection to the remote computer in such a way that a local terminal appears to be at the remote side.
Difference between telnet & ssh?


